Terraform - S3 & DynamoDB for Remote State Storage & Locking ¶
Overview ¶
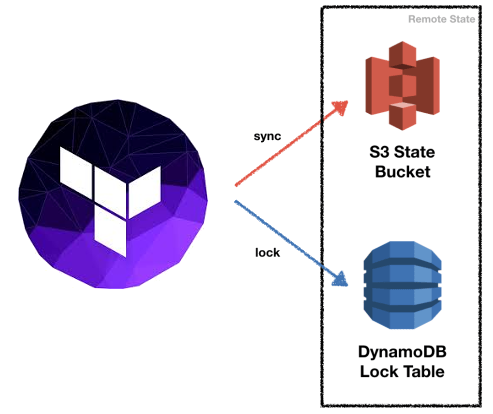
Use this terraform configuration files to create the S3 bucket & DynamoDB table needed to use Terraform Remote State Storage & Locking.
Prerequisites ¶
Terraform repo structure + state backend initialization
- Ensure you have
Leverage CLIinstalled in your system - Refer to Configuration Pre-requisites to understand how to set up the configuration files required for this layer.
- Leveraged by the Infrastructure as Code (IaC) Library through the terraform-aws-tfstate-backend module
Set up ¶
Steps to initialize your tf-backend
- At the corresponding account dir, eg: /hcp/base-tf-backend then,
- Run
leverage terraform init - Run
leverage terraform plan, review the output to understand the expected changes - Run
leverage terraform apply, review the output once more and typeyesif you are okay with that -
This should create a
terraform.tfstatefile in this directory but we don't want to push that to the repository so let's push the state to the backend we just created- Open
config.tfand uncomment the following lines:# backend "s3" { # key = "hcp/tf-backend/terraform.tfstate" # } - Run
leverage terraform initand typeyeswhen Terraform asks if you want to import the state to the S3 backend - Done. You can remove
terraform.tfstatenow (and alsoterraform.tfstate.backupif available)
- Open
 this tape must be updated
this tape must be updated