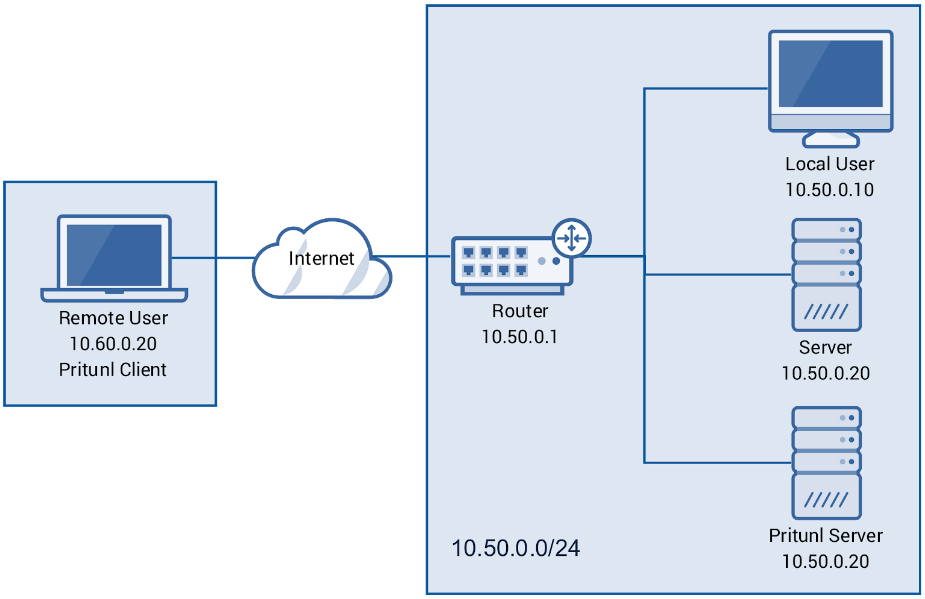
VPN Server ¶
To securely and scalable privately access AWS Cross Organization resources we’ll implement Pritunl VPN Server ¶
Security Directives
- Private HTTP endpoints for Applications (FrontEnd + APIs), SSH, monitoring & logging (UI / Dashboards) among others. Eg: Jenkins, DroneCI, EFK, Prometheus, Spinnaker, Grafana.
- K8s API via kubectl private endpoint eg: avoiding emergency K8s API vulnerability patching.
-
Limit exposure: Limit the exposure of the workload to the internet and internal networks by only allowing minimum required access -> Avoiding exposure for Dev/QA/Stg http endpoints
- The Pritunl OpenVPN Linux instance is hardened and only runs this VPN solution. All other ports/access is restricted.
- Each VPN user can be required to use MFA to connect via VPN (as well as strong passwords). This combination makes almost impossible for an outsider to gain access via VPN.
- Centralized access and audit logs.