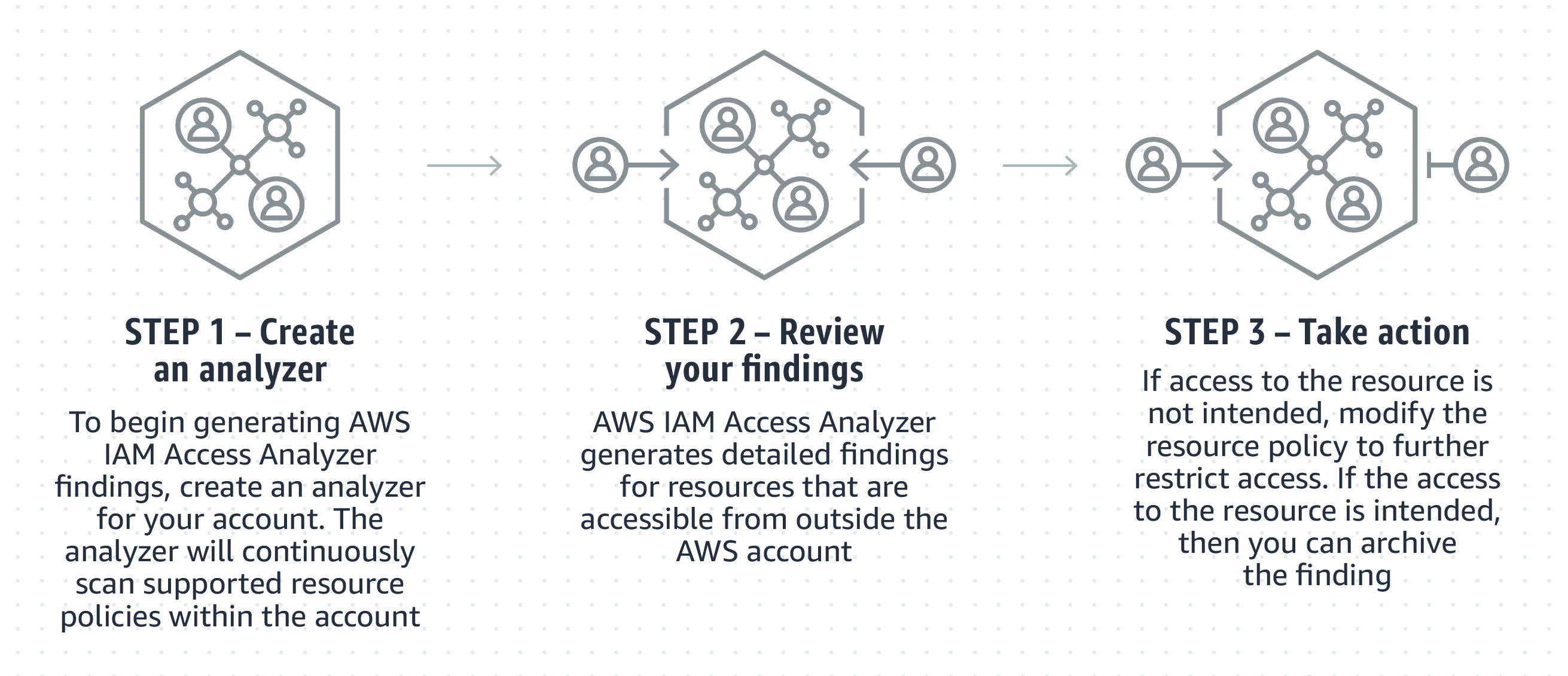
IAM Access Analyzer ¶
Overview ¶
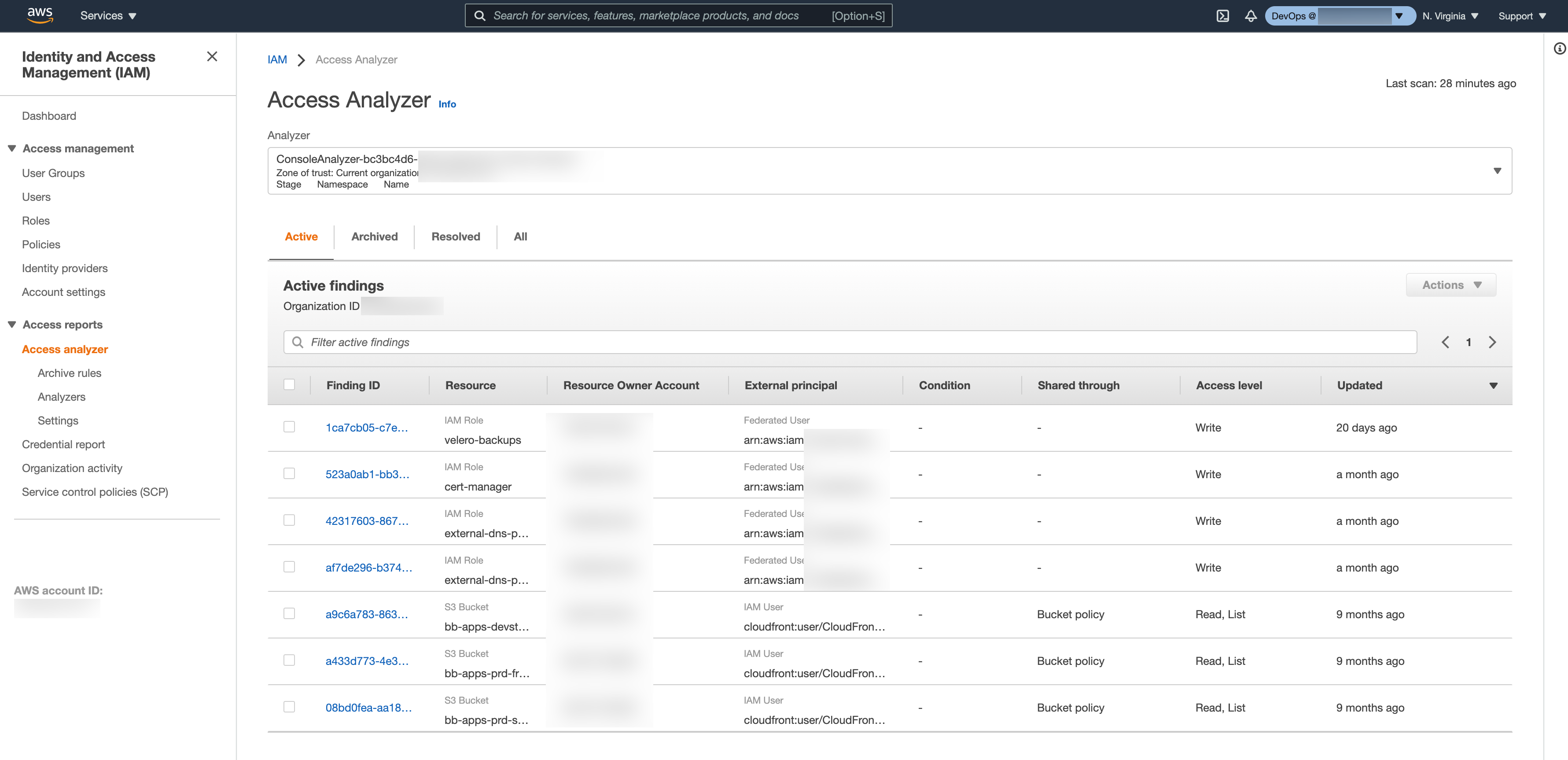
Access Analyzer analyzes the resource-based policies that are applied to AWS resources in the Region where you enabled Access Analyzer. Only resource-based policies are analyzed.
Supported resource types:
- Amazon Simple Storage Service buckets
- AWS Identity and Access Management roles
- AWS Key Management Service keys
- AWS Lambda functions and layers
- Amazon Simple Queue Service queues
- AWS Secrets Manager secrets
AWS Organizations ¶
CONSIDERATION: AWS Organization integration
In order to enable AccessAnalyzer with the Organization at the zone of of trust in the Security account, this account needs to be set as a delegated administrator.
Such step cannot be performed by Terraform yet so it was set up manually as described below: https://docs.aws.amazon.com/IAM/latest/UserGuide/access-analyzer-settings.html
If you're configuring AWS IAM Access Analyzer in your AWS Organizations management account, you can add a member account in the organization as the delegated administrator to manage Access Analyzer for your organization. The delegated administrator has permissions to create and manage analyzers with the organization as the zone of trust. Only the management account can add a delegated administrator.
Reference Architecture implementation code ¶
Reference Architecture Code: le-tf-infra-aws/security/security-base/iam_access_analizer.tf
resource "aws_accessanalyzer_analyzer" "default" {
analyzer_name = "ConsoleAnalyzer-bc3bc4d6-09cb-XXXX-XXXX-XXXXXXXXXX"
type = "ORGANIZATION"
tags = local.tags
}
AWS Web Console ¶