Identity and Access Management (IAM) Layer ¶
Setting up user credentials ¶
Please follow the steps below to orchestrate your base-identities layer 1st in your
project-root AWS account and
afterwards in your project-security account.
IAM user standard creation workflow
- Pre-requisite add Public PGP Key following the documentation
- For steps 3. and 4. consider following Leverage's Terraform workflow
- Update (add | remove) your IAM Users associated code and deploy
security/global/base-identities/users.tf
Consider customizing your account Alias and Password Policy
- Update (add | remove | edit) your IAM Groups associated code and deploy security/global/base-identities/groups.tf
- Get and share the IAM Users AWS Console user id and its OTP associated password from the
make applyoutputstemporally set
sensitive = falseto get the encrypted outputs in your prompt output.
- Each user will need to decrypt its AWS Console Password, you could share the associated documentation with them.
- Users must login to the AWS Web Console (https://project-security.signin.aws.amazon.com/console) with their decrypted password and create new pass
- Activate MFA for Web Console (Optional but strongly recommended)
- User should create his AWS ACCESS KEYS if needed
- User could optionally set up
~/.aws/project/credentials+~/.aws/project/configfollowing the immediately below AWS Credentials Setup sub-section - To allow users to
Access AWS Organization member account
consider repeating step 3. but for the corresponding member accounts:
Recommended Post-tasks ¶
Deactivating AWS STS in not in use AWS Region
When you activate STS endpoints for a Region, AWS STS can issue temporary credentials to users and roles in your account that make an AWS STS request. Those credentials can then be used in any Region that is enabled by default or is manually enabled. You must activate the Region in the account where the temporary credentials are generated. It does not matter whether a user is signed into the same account or a different account when they make the request.
To activate or deactivate AWS STS in a Region that is enabled by default (console)
- Sign in as a root user or an IAM user with permissions to perform IAM administration tasks.
- Open the IAM console and in the navigation pane choose Account settings.
- If necessary, expand Security Token Service (STS), find the Region that you want to activate, and then choose Activate or Deactivate. For Regions that must be enabled, we activate STS automatically when you enable the Region. After you enable a Region, AWS STS is always active for the Region and you cannot deactivate it. To learn how to enable a Region, see Managing AWS Regions in the AWS General Reference.


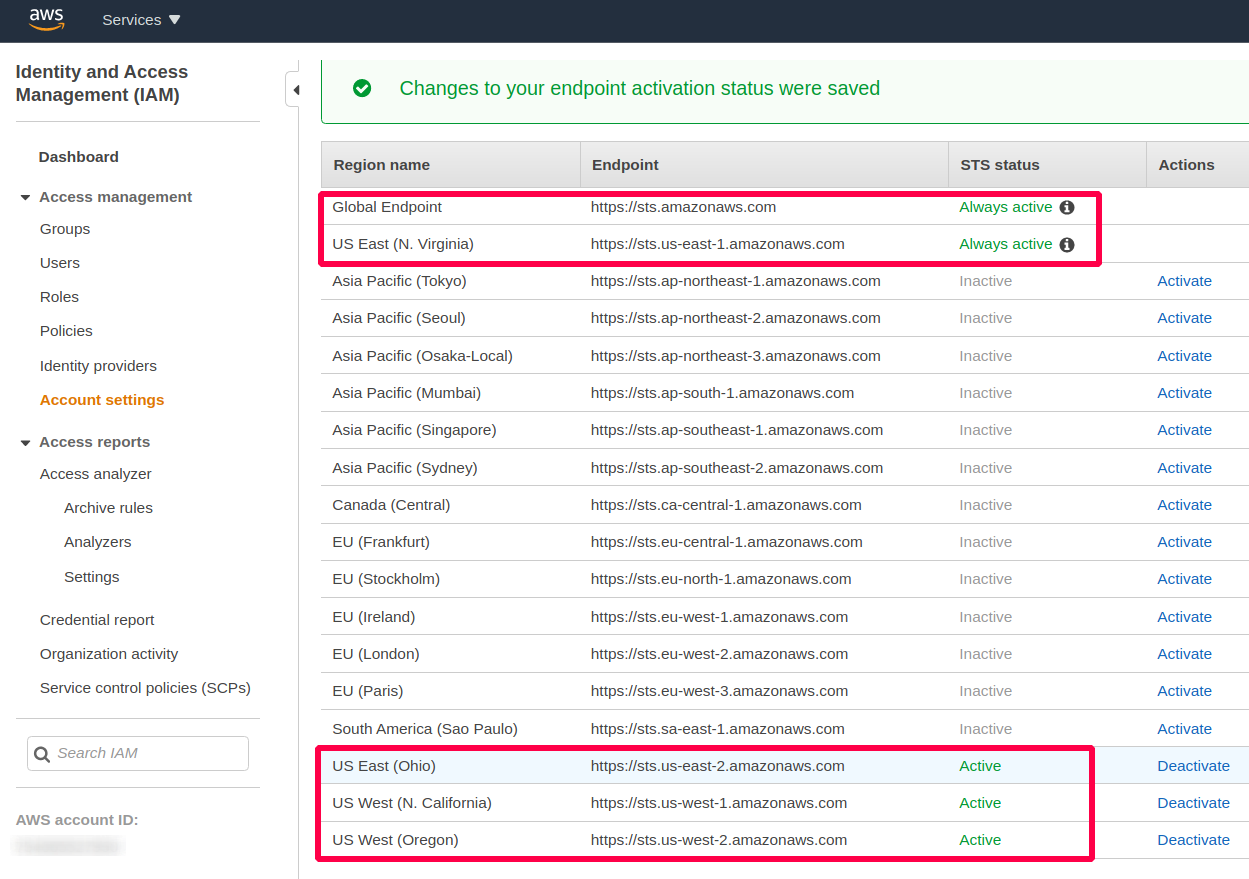
Figure: Deactivating AWS STS in not in use AWS Region. Only in used Regions must have STS activated.
