AWS SSO ¶
Important
Parts of this documentation are outdated. JumpCloud is no longer part of our reference architecture.
Single Sign-On (SSO) ¶
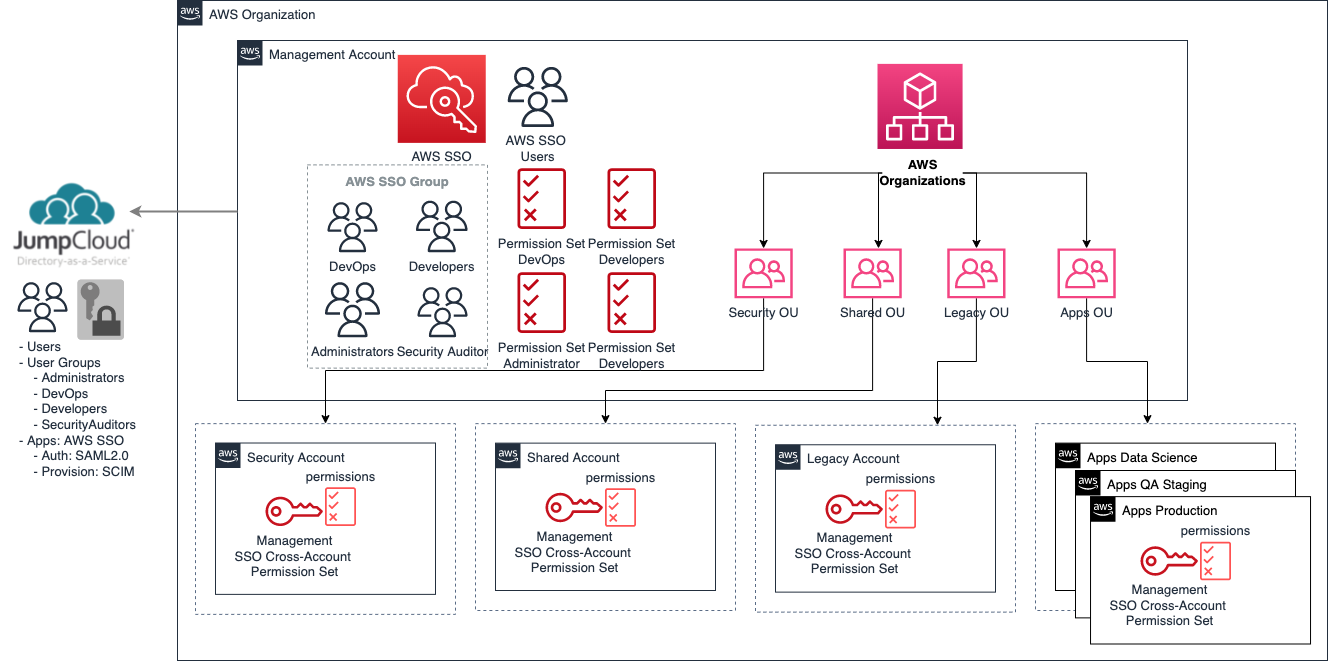
JumpCloud will be configured as the Identity Provider (IdP) that we will integrate with AWS SSO in order to grant users access to AWS resources from a centralized service. Users will be able to log in to JumpCloud in order to access AWS accounts, using specific permission sets that will in turn determine what kind of actions they are allowed on AWS resources.
SSO Strengths ¶
- 100% cloud-based
- Secure directory services
- Unified device management
- SSO and user lifecycle management
- Secure app and server authentication with cloud LDAP
- Event logging, reporting, and monitoring
SSO Users ¶
Users will be defined in JumpCloud and used for deploying AWS resources with scoped permissions.
SSO Groups ¶
| Account / Groups | Administrators | DevOps | FinOps | SecurityAuditors |
|---|---|---|---|---|
| Management | x | x | x | x |
Consideration
This definition could be fully customized based on the project specific needs
SSO Permission Sets (w/ Account Associations) ¶
| Account / Permission Sets | Administrator | DevOps | FinOps | SecurityAuditors |
|---|---|---|---|---|
| Management | x | x | ||
| Security | x | x | x | |
| Shared | x | x | x | |
| Network | x | x | x | |
| Apps-DevStg | x | x | x | |
| Apps-Prd | x | x | x |
Considerations
- Devops Engineers will assume this permission set through JumpCloud + AWS SSO.
- Developers could have their specific SSO Group + Permission Set policy association.
- This definition could be fully customized based on the project specific needs